The ability to enable or perform DHCP Snooping is one of those really cool and powerful features we find on Catalyst Switches such as 2900’s, 3500, and 3700’s Switches that often gets overlooked. This simple yet powerful feature can help prevent malicious, and none malicious attacks along with the prevention of DHCP starvation or DHCP Denial Of Service (DoS) attaches. The really nice thing about this feature is it incredibly simple to implement.
Trusted vs Untrusted
The concept or idea is pretty simple. You either trust the port or not it’s that simple, however there are a few steps that need to be taken before you can turn on DHCP Snooping. One of the really nice features with regards to DHCP Snooping is that interfaces are un-trusted by default. The reason this is so important is the fact that you don’t have to configure each individual un-trusted port on the Switch.
Lets start off by enabling DHCP Snooping globally on Switch SW1
SW1#configure terminal
SW1(config)#ip dhcp snooping
SW1(config)#end
SW1#
Local vs Remote
The next step in setting up DHCP Snooping is the creation of the snooping database were bindings, and statistics will be stored. Depending on your environment you have a couple of options to choose from when storing the snooping database. Option # 1 would be storing the database locally on local Flash of the Switch. Option # 2 would be to store the database remotely via TFTP, FTP, HTTP etc… I’ll demonstrate using creating the database locally as well as off box.
Database Option # 1
SW1#configure terminal
SW1(config)#ip dhcp snooping database flash:/snooping.db
SW1(config)#end
SW1#
Database Option # 2
SW1#configure terminal
SW1(config)#ip host SERVER 172.18.0.20
SW1(config)#ip ftp username snoopdog
SW1(config)#ip ftp password snooping
SW1(config)#ip dhcp snooping database ftp://SERVER/snooping.db
SW1(config)#end
SW1#
Now that snooping database has been created lets take a look at the Flash filesystem on the Switch
SW1#dir flash:/snooping.db
Directory of flash:/snooping.db
5 -rwx 43 Oct 4 2014 9:11:13 -05:00 snooping.db
122185728 bytes total (98681344 bytes free)
SW1#
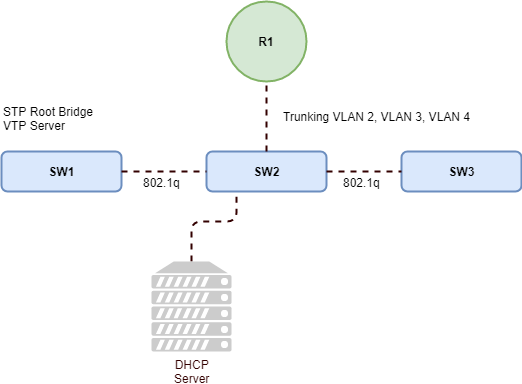
One of the key configuration steps when enabling DHCP Snooping is making sure that those VLAN’s that need to be monitored for unauthorized DHCP activity are included in snooping processes. This can been accomplished by simply enabling snooping on a per VLAN basis. So based on the above diagram we can simply enable snooping as follows.
SW1#configure terminal
SW1(config)#ip dhcp snooping vlan 2-4
SW1(config)#end
SW1#
Now that the preliminary configurations have been completed we can move forward with enabling DHCP Snooping on those interfaces that should be trusted or expected to provide legitimate DHCP request to Clients. We need to take special care to enable those ports that are acting as Layer 2 802.1Q Trunks between downstream Switches along with Trunk between the Switch and the Router.
Lets start off by trusting the 802.1q trunking interface between Switch SW1 and the Router R1
SW1#configure terminal
SW1(config)#interface gi1/0/1
SW1(config-if)#ip dhcp snooping trust
SW1(config-if)#end
SW1#
Now we can move onto the 802.1Q Trunk ports between Switch SW1, SW2, and SW3. Lets assume from the diagram above the the 802.1q Trunking ports between Switch SW1, SW2, and SW3 are on ports Gi1/0/49, and Gi1/0/50. Remember we only need to enable trusted ports downstream from the Root Switch in this case Switch SW1.
SW1#configure terminal
SW1(config)#interface range gi1/0/49 - 50
SW1(config-if-range)#ip dhcp snooping trust
SW1(config-if)#end
SW1#
Now that we have have enabled the trusted interfaces that we expect to see legitimate DHCP request on lets take a look at the operational status of the interfaces, along with the monitored VLAN we configured earlier.
SW1#show ip dhcp snooping
Switch DHCP snooping is enabled
DHCP snooping is configured on following VLANs:
2-4
DHCP snooping is operational on following VLANs:
2-4
DHCP snooping is configured on the following L3 Interfaces
Insertion of option 82 is enabled
circuit-id default format: vlan-mod-port
remote-id: 84c8.17c5.a480 (MAC)
Option 82 on untrusted port is not allowed
Verification of hwaddr field is enabled
Verification of giaddr field is enabled
DHCP snooping trust/rate is configured on the following Interfaces
----------------------- ------- ------------ ----------------
GigabitEthernet1/0/1 yes yes unlimited
Custom circuit-ids:
GigabitEthernet1/0/49 yes yes unlimited
Custom circuit-ids:
GigabitEthernet1/0/50 yes yes unlimited
Custom circuit-ids:
Now lets take a look at the current list of DHCP bindings stored in the snooping database we created earlier.
SW1#show ip dhcp snooping binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
---------------------- ------------- ---------- -------- ----- --------------------
A0:55:4C:8C:68:BE 172.18.0.51 352732 dhcp-snooping 2 GigabitEthernet1/0/10
AC:44:B2:13:BA:0F 172.19.0.50 691019 dhcp-snooping 3 GigabitEthernet1/0/18
A0:54:4B:8C:45:62 172.19.0.51 352733 dhcp-snooping 3 GigabitEthernet1/0/20
A0:55:4B:8C:82:6F 172.20.0.50 352722 dhcp-snooping 4 GigabitEthernet1/0/22
From the above output we can see the DHCP Snooping process has learned about the following DHCP Clients their respective MAC addresses along with the interfaces the request originated from. Happy snooping.
I hope you found this post on DHCP Snooping helpful and informative. Be sure to let me know what you think by leaving suggestions, and feedback in the comments section below. You can find out more about these and other articles be checking out recent posts and archives. To learn more about me be sure to check out the About page. And as always thanks again for visiting The Packet.
